Simulation of 5G/6G Wireless Networks
Published:
A list of all the posts and pages found on the site. For you robots out there is an XML version available for digesting as well.
Published:
Bachelor of Engineering Degree, Universiti Brunei Darussalam, 2021
Published:
Tweets Analyzer
Published:
Neural network models
Bachelor of Engineering Degree, Universiti Brunei Darussalam, 2022
Published:
Security: Algorithmic Trojans, Memory Leak, Packet Drop
Bachelor of Engineering Degree, online, 2022
Published:
Computer Networks and Machine Learning.
Bachelor of Science Degree, Marist College, 2025
Master of Science Computer Science(MSCS), Marist College, 2024
Published:
Published:
Published:
, , 2024
Published:
Page not found. Your pixels are in another canvas.
This is a page not in th emain menu
Published:
Advising@Marist
Published:
Internship@Marist
Published:
This post covers .
Published:
This post covers .
Published:
Published:
Published:
Published:
This post covers Mobile and Wireless Networks by Khaldoun Al Agh, Guy Pujolle, and Tara Ali-Yahiya.
Published:
This post covers Mobile and Wireless Networks by Khaldoun Al Agh, Guy Pujolle, and Tara Ali-Yahiya.
Published:
Published:
This post covers WIRELESS COMMUNICATIONS AND NETWORKS by William Stallings.
Published:
This post covers WIRELESS COMMUNICATIONS AND NETWORKS by William Stallings.
Published:
This post covers WIRELESS COMMUNICATIONS AND NETWORKS by William Stallings.
Published:
This post covers WIRELESS COMMUNICATIONS AND NETWORKS by William Stallings.
Published:
This post covers Mobile and Wireless Networks by Khaldoun Al Agh, Guy Pujolle, and Tara Ali-Yahiya.
Published:
This post covers Mobile and Wireless Networks by Khaldoun Al Agh, Guy Pujolle, and Tara Ali-Yahiya.
Published:
Published:
This post covers Mobile and Wireless Networks by Khaldoun Al Agh, Guy Pujolle, and Tara Ali-Yahiya.
Published:
Published:
This post covers Mobile and Wireless Networks by Khaldoun Al Agh, Guy Pujolle, and Tara Ali-Yahiya.
Published:
This post covers Mobile and Wireless Networks by Khaldoun Al Agh, Guy Pujolle, and Tara Ali-Yahiya.
Published:
This post covers Wireless Communications: Principles and Practices by Theodore S. Rapport.
Published:
This post covers Wireless Communications: Principles and Practices by Theodore S. Rapport.
Published:
This post covers Wireless Communications: Principles and Practices by Theodore S. Rapport.
Published:
This post covers WIRELESS COMMUNICATIONS AND NETWORKS by William Stallings.
Published:
This post covers WIRELESS COMMUNICATIONS AND NETWORKS by William Stallings.
Published:
This post covers WIRELESS COMMUNICATIONS AND NETWORKS by William Stallings.
Published:
This post covers WIRELESS COMMUNICATIONS AND NETWORKS by William Stallings.
Published:
This post covers WIRELESS COMMUNICATIONS AND NETWORKS by William Stallings.
Published:
This post covers WIRELESS COMMUNICATIONS AND NETWORKS by William Stallings.
Published:
This post covers Wireless Communications: Principles and Practices by Theodore S. Rapport.
Published:
This post covers Wireless Communications: Principles and Practices by Theodore S. Rapport.
Published:
This post covers Wireless Communications: Principles and Practices by Theodore S. Rapport.
Published:
This post covers Wireless Communications: Principles and Practices by Theodore S. Rapport.
Published:
This post covers Wireless Communications: Principles and Practices by Theodore S. Rapport.
Published:
This post covers Wireless Communications: Principles and Practices by Theodore S. Rapport.
Published:
This post covers Wireless Communications: Principles and Practices by Theodore S. Rapport.
Published:
This post covers WIRELESS COMMUNICATIONS AND NETWORKS by William Stallings.
Published:
This post covers WIRELESS COMMUNICATIONS AND NETWORKS by William Stallings.
Published:
This post covers WIRELESS COMMUNICATIONS AND NETWORKS by William Stallings.
Published:
This post covers WIRELESS COMMUNICATIONS AND NETWORKS by William Stallings.
Published:
This post covers Mobile and Wireless Networks by Khaldoun Al Agh, Guy Pujolle, and Tara Ali-Yahiya.
Published:
This post covers Wireless Communications: Principles and Practices by Theodore S. Rapport.
Published:
This post covers MOBILE AD HOC NETWORKING by STEFANO BASAGNI.
Published:
This post covers MOBILE AD HOC NETWORKING by STEFANO BASAGNI.
Published:
This post covers WIRELESS COMMUNICATIONS AND NETWORKS by Williant Stallings.
Published:
Published:
This post covers WIRELESS COMMUNICATIONS AND NETWORKS by William Stallings.
Published:
This post covers WIRELESS COMMUNICATIONS AND NETWORKS by William Stallings.
Published:
This post covers .
Published:
This post covers Wireless Communications: Principles and Practices by Theodore S. Rapport.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers data reported on Twitter by Brunei media.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
Published:
This post covers Introduction to probability from Statistics for Engineers and Scientists by William Navidi.
U.S. Patent Publication, 2015
The patent describes a safe card that that by default is in a blocked state so that no transcation can be made. The safe card can be activated for a limited time by an authorized user for the transaction.
Recommended citation: Aneja, N., and Aneja, S. "Anti-fraud computer implemented method for financial card transaction." U.S. Patent Publication 2015/0339,657, filed May 23, 2014, published Nov 26, 2015. https://patentimages.storage.googleapis.com/06/22/8e/674c30a57d0fe8/US20150339657A1.pdf
U.S. Issued Patent, 2020
The discloosure presents unified instant messaging application/service that enables to concurrently send messages via online mode using internet and Offline or Airplane mode
Recommended citation: Aneja, S., Aneja. N., and Petra, I. "Instant messaging for mobile device with offline and online mode." U.S. Patent 10,834,035, filed Dec 28, 2015, issued Nov 10, 2020. https://patentimages.storage.googleapis.com/58/d4/f7/58ebe5626a9362/US10834035.pdf
Detecting Fake News using language features 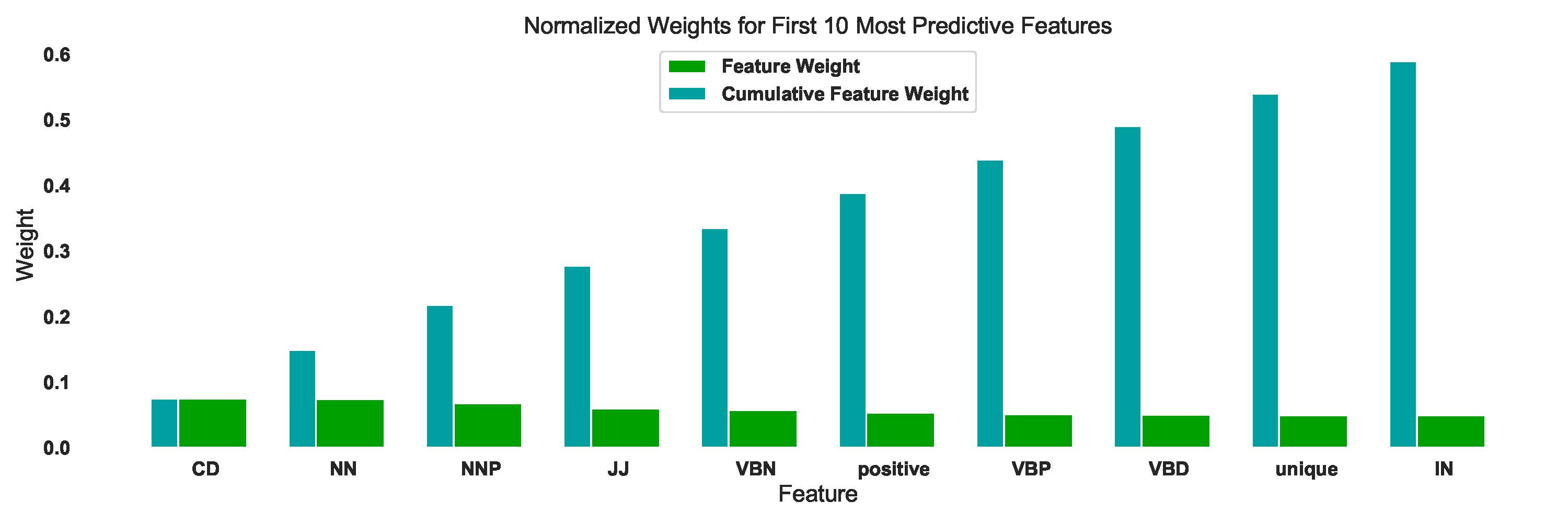
Published:
Security: Algorithmic Trojans, Memory Leak, Packet Drop
Published:
Computer Networks and Machine Learning.
Published in Security and Communication Networks, 2011
Recommended citation: Khurana, S., & Gupta, N. (2011). " End-to-end protocol to secure ad hoc networks against wormhole attacks. " Security and Communication Networks, 4(9), 994-1002. https://onlinelibrary.wiley.com/doi/epdf/10.1002/sec.272
Published in 20th Annual International Conference on High Performance Computing, 2013
Recommended citation: Singhal, S., Real, L. V., George, T., Aneja, S., & Sabharwal, Y. (2013). " A hybrid parallelization approach for high resolution operational flood forecasting. " In 20th Annual International Conference on High Performance Computing (pp. 405-414). IEEE. https://ieeexplore.ieee.org/document/6799142
Published in European Conference on Parallel Processing 2014, 2014
Recommended citation: Singhal S., Aneja S., Liu F., Real L.V., George T. (2014). " IFM: A Scalable High Resolution Flood Modeling Framework. " In: Silva F., Dutra I., Santos Costa V. (eds) Euro-Par 2014 Parallel Processing. Euro-Par 2014. Lecture Notes in Computer Science, vol 8632. Springer, Cham. https://doi.org/10.1007/978-3-319-09873-9_58 . https://link.springer.com/chapter/10.1007/978-3-319-09873-9_58
Published in Wireless Networks, 2015
Recommended citation: Nagrath, P., Aneja, S., Gupta, N. (2016). " Protocols for mitigating blackhole attacks in delay tolerant networks. " Wireless Networks 22, 235–246. . https://link.springer.com/article/10.1007/s11276-015-0959-3
Published in EURASIP Journal on Wireless Communications and Networking, 2015
Recommended citation: Johari, R., Gupta, N. & Aneja, S. (2015). " CONCOR: context-aware community-oriented routing for intermittently connected network. " J Wireless Com Network 2015, 148. . https://jwcn-eurasipjournals.springeropen.com/articles/10.1186/s13638-015-0357-7
Published in International Journal of Distributed Sensor Networks, 2015
Recommended citation: Johari, R., Gupta, N., Aneja, S. (2015). " POSOP Routing Algorithm: A DTN Routing Scheme for Information Connectivity of Health Centres in Hilly State of North India. " International Journal of Distributed Sensor Networks, 11(6), 376861.. https://journals.sagepub.com/doi/full/10.1155/2015/376861
Published in Wireless Personal Communications, 2015
Recommended citation: Johari, S.R., Gupta, N. & Aneja, S. (2015). " Experimental Evaluation of Routing Schemes for Intermittently Connected Wireless Mobile Networks. " Wireless Pers Commun 87, 897–921 (2016). https://link.springer.com/article/10.1007%2Fs11277-015-3109-4
Published in Wireless Network, 2019
Recommended citation: Aneja, S., Nagrath, P. & Purohit, G.N. (2019). " Energy efficient reputation mechanism for defending different types of flooding attack." Wireless Networks 25, 3933–3951 (2019). https://link.springer.com/article/10.1007%2Fs11276-018-01928-x
Published in International Journal of Security and Networks (IJSN), 2020
Recommended citation: Preeti Nagrath; Sandhya Aneja; G.N. Purohit (2020). " Taxonomy of reputation-based defending mechanisms against types of attacks in delay tolerant networks." International Journal of Security and Networks (IJSN), Vol. 16, No. 2, 2021. https://www.inderscience.com/offer.php?id=116772
Published in Data in Brief, 2021
This paper presents network traffic traces data of D-Link IoT devices from packet and frame levels.
Recommended citation: Rajarshi Roy Chowdhury, Sandhya Aneja, Nagender Aneja, and Pg Emeroylariffion Abas (2021). " Packet-level and IEEE 802.11 MAC frame-level network traffic traces data of the D-Link IoT devices." Data in Brief, Volume 37, Aug 2021, 107208, ISSN 2352-3409, doi: 10.1109/IOTAIS.2018.8600824. https://www.sciencedirect.com/science/article/pii/S2352340921004923
Published in International Journal of Communication Networks and Distributed Systems (IJCNDS), 2021
Recommended citation: Sandhya Aneja, Nagender Aneja, Bharat K. Bhargava, Rajarshi Roy Chowdhury (2021). " Device Fingerprinting using Deep Convolutional Neural Networks." International Journal of Communication Networks and Distributed Systems(IJCNDS), Vol. 28, No. 2, 2021. https://www.inderscience.com/info/ingeneral/forthcoming.php?jcode=ijcnds
Published in Wireless Communications and Mobile Computing, 2023
Recommended citation: Nagender Aneja, Sandhya Aneja, Bharat K. Bhargava (2023). " AI‐Enabled Learning Architecture Using Network Traffic Traces over IoT Network: A Comprehensive Review." Wireless Communications and Mobile Computing, Vol. 2023, 2023. https://onlinelibrary.wiley.com/doi/pdf/10.1155/2023/8658278
Published in International Journal of Intelligent Networks, 2023
Recommended citation: Wang Xin Hui, Nagender Aneja, Sandhya Aneja, Abdul Ghani Naim (2023). " Conversational chat system using attention mechanism for COVID-19 inquiries." International Journal of Intelligent Networks, Vol.4, Pages 140-144, 2023. https://www.sciencedirect.com/science/article/pii/S266660302300012X
Master of Science (M.S.), Marist College, 2022
The course covers key topics in the field of Data Communication MSIT 567N course.
Bachelor of Science (B.S.), Marist College, 2022
The course covers key topics in the field of Introduction to Programming.
Master of Science (M.S.), Marist College, 2023
The course covers key topics in the field of advanced data structures.
Bachelor of Science (B.S.), Marist College, 2024
The course covers key topics in the field of Data Communication and networking.
Master of Science (M.S.), Marist College, 2024
The course covers key topics in the field of Networking.