MAC protocol CSMA/CA
Published:
This post covers WIRELESS COMMUNICATIONS AND NETWORKS by William Stallings.
Basic Ideas
The Wireless LAN- Fundamental System Design

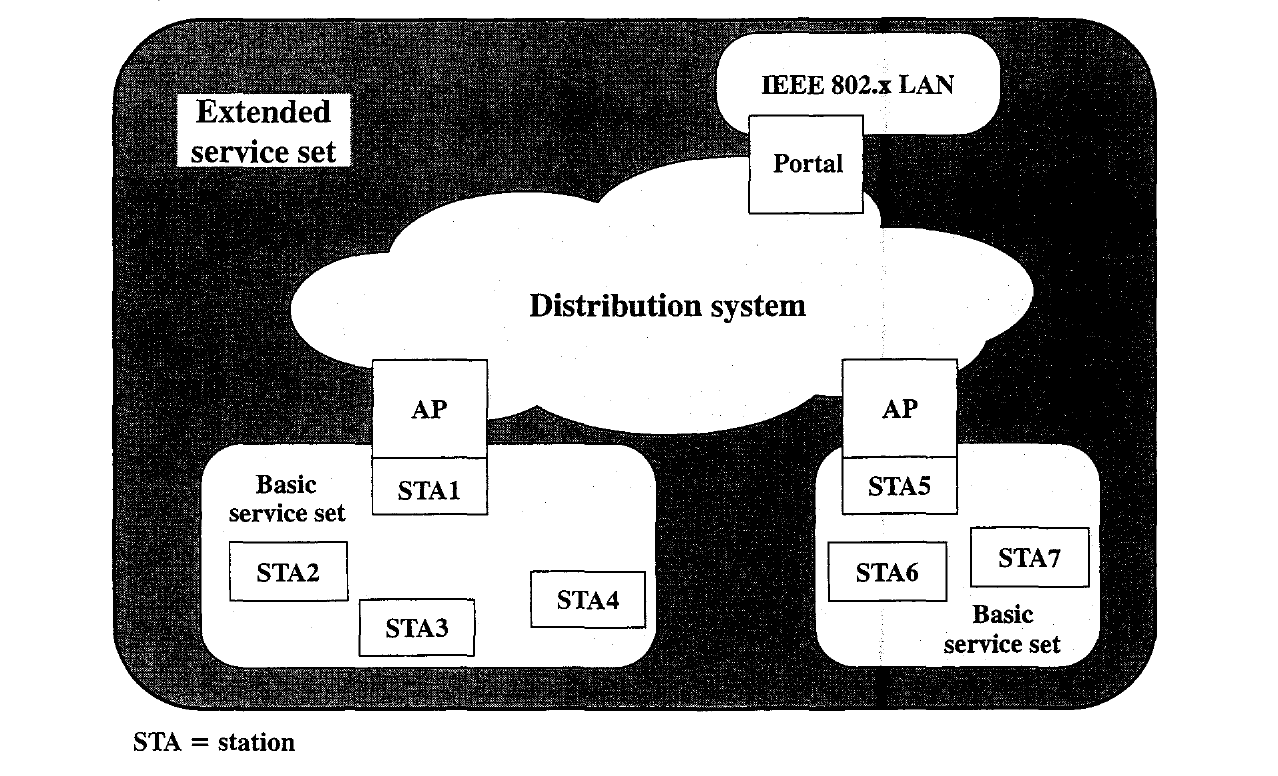
The smallest building block of a wireless LAN is a basic service set (BSS), which consists of some number of stations executing the same MAC protocol and competing for access to the same shared wireless medium.
A BSS may be isolated or it may connect to a backbone distribution system (DS) through an access point (AP).
The AP functions as a bridge and a relay point. In a BSS, client stations do not communicate directly with one another.

Rather, if one station in the BSS wants to communicate with another station in the same BSS, the MAC frame is first sent from the originating station to the AP, and then from the AP to the destination station.
Similarly, a MAC frame from a station in the BSS to a remote station is sent from the local station to the AP and then relayed by the AP over the DS on its way to the destination station.
The BSS generally corresponds to what is referred to as a cell in the literature. The DS can be a switch, a wired network, or a wireless network.
When all the stations in the BSS are mobile stations, with no connection to other BSSs, the BSS is called an independent BSS (IBSS).
An IBSS is typically an ad hoc network. In an IBSS, the stations all communicate directly, and no AP is involved.
A simple configuration is shown in above Figure, in which each station belongs to a single BSS; that is, each station is within wireless range only of other stations within the same BSS.
It is also possible for two BSSs to overlap geographically, so that a single station could participate in more than one BSS.
Further, the association between a station and a BSS is dynamic. Stations may turn off, come within range, and go out of range.
An extended service set (ESS) consists of two or more basic service sets interconnected by a distribution system.
Typically, the distribution system is a wired backbone LAN but can be any communications network.
The extended service set appears as a single logical LAN to the logical link control (LLC) level.
Figure indicates that an access point (AP) is implemented as part of a station; the AP is the logic within a station that provides access to the DS by providing DS services in addition to acting as a station.
To integrate the IEEE 802.11 architecture with a traditional wired LAN, a portal is used. The portal logic is implemented in a device, such as a bridge or router, that is part of the wired LAN and that is attached to the DS.
Distribution of Messages within a DS
- Distribution is the primary service used by stations to exchange MAC frames when the frame must traverse the DS to get from a station in one BSS to a station in another BSS. For example, suppose a frame is to be sent from station 2 (STA 2) to STA 7 in Figure. The frame is sent from STA 2 to STA 1, which is the AP for this BSS.The AP gives the frame to the DS, which has the job of directing the frame to the AP associated with STA 5 in the target BSS. STA 5 receives the frame and forwards it to STA 7.
- If the two stations that are communicating are within the same BSS, then the distribution service logically goes through the single AP of that BSS.
- Integration: enables transfer of data between a station on an IEEE 802.11 LAN and a station on an integrated IEEE 802.x LAN.
- Association related Services The primary purpose of the MAC layer is to transfer MSDUs between MAC entities; this purpose is fulfilled by the distribution service. For that service to function, it requires information about stations within the ESS, which is provided by the association-related services.
- Before the distribution service can deliver data to or accept data from a station, that station must be associated. Before looking at the concept of association, we need to describe the concept of mobility. The standard defines three transition types based on mobility:
- No transition: A station of this type is either stationary or moves only within the direct communication range of the communicating stations of a single BSS.
- BSS transition: This is defined as a station movement from one BSS to another BSS within the same ESS. In this case, delivery of data to the station requires that the addressing capability be able to recognize the new location of the station
ESS transition: This is defined as a station movement from a BSS in one ESS to a BSS within another ESS. This case is supported only in the sense that the station can move. Maintenance of upper-layer connections supported by 802.11 cannot be guaranteed. In fact, disruption of service is likely to occur.
Authentication: Used to establish the identity of stations to each other.
Deauthentication: This service is invoked whenever an existing authentication is to be terminated.
- Disassociation: A notification from either a station or an AP that an existing association is terminated. A station should give this notification before leaving an ESS or shutting down.
IEEE 802.11 defines three services that provide a wireless LAN with these two features:
- There are two characteristics of a wired LAN that are not inherent in a wireless LAN.
- 1.In order to transmit over a wired LAN, a station must be physically connected to the LAN. On the other hand, with a wireless LAN, any station within radio range of the other devices on the LAN can transmit.
- In a sense, there is a form of authentication with a wired LAN, in that it requires some positive and presumably observable action to connect a station to a wired LAN.
- 2.Similarly, in order to receive a· transmission from a station that is part of wired LAN, the receiving station must also be attached to the wired LAN. On the other hand, with a wireless LAN, any station within radio range can receive.
- Thus, a wired LAN provides a degree of privacy, limiting reception of data to stations connected to the LAN.
- Authentication: Used to establish the identity of stations to each other.
Privacy: Used to prevent the contents of messages from being read by other than the intended recipient.
- Reassocation: Enables an established association to be transferred from one AP to another, allowing a mobile station to move from one BSS to another.
MEDIUM ACCESS CONTROL
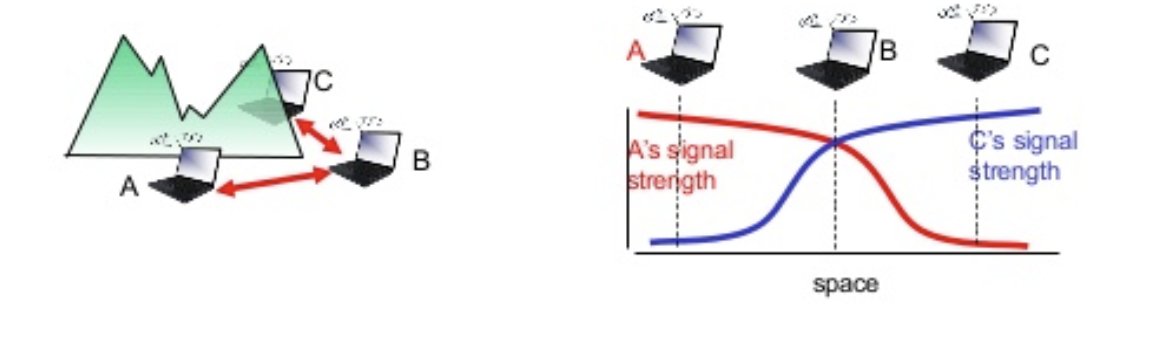
Reliable Data Delivery: As with any wireless network, a wireless LAN using the IEEE 802.11 physical and MAC layers is subject to considerable unreliability.
Noise, interference, and other propagation effects result in the loss of a significant number of frames.
Even with error-correction codes, a number of MAC frames may not successfully be received.
This situation can be dealt with by reliability mechanisms at a higher layer, such as TCP.
However, timers used for retransmission at higher layers are typically on the order of seconds
IEEE 802.11 includes a frame exchange protocol. When a station receives a data frame from another station, it returns an acknowledgment (ACK) frame to the source station.
it returns an acknowledgment (ACK) frame to the source station. This exchange is treated as an atomic unit, not to be interrupted by a transmission from any other station.
If the source does not receive an ACK within a short period of time, either because its data frame was damaged or because the returning ACK was damaged, the source retransmits the frame.
Thus, the basic data transfer mechanism in IEEE 802.11 involves an exchange of two frames.
To further enhance reliability, a four-frame exchange may be used. In this scheme, a source first issues a request to send (RTS) frame to the destination.
The destination then responds with a clear to send (CTS). After receiving the CTS, the source transmits the data frame, and the destination responds with an ACK.The RTS alerts all stations that are within reception range of the source that an exchange is under way these stations refrain from transmission in order to avoid a collision between two frames transmitted at the same time.

Similarly, the CTS alerts all stations that are within reception range of the destination that an exchange is under way. The RTS/CTS portion of the exchange is a required function of the MAC but may be disabled.
Medium Access Control: The 802.11 working group considered two types of proposals for a MAC algorithm: distributed access protocols, which, like Ethernet, distribute the decision to transmit over all the nodes using a carrier-sense mechanism; and centralized access protocols, which involve regulation of transmission by a centralized decision maker.
A distributed access protocol makes sense for an ad hoc network of peer workstations (typically an IBSS) and may also be attractive in other wireless LAN configurations than consist primarily of bursty traffic.
A centralized access protocol is natural for configurations in which a number of wireless stations are interconnected with each other and some sort of base station that attaches to a backbone wired LAN;
it is especially useful if some of the data is time sensitive or high priority.
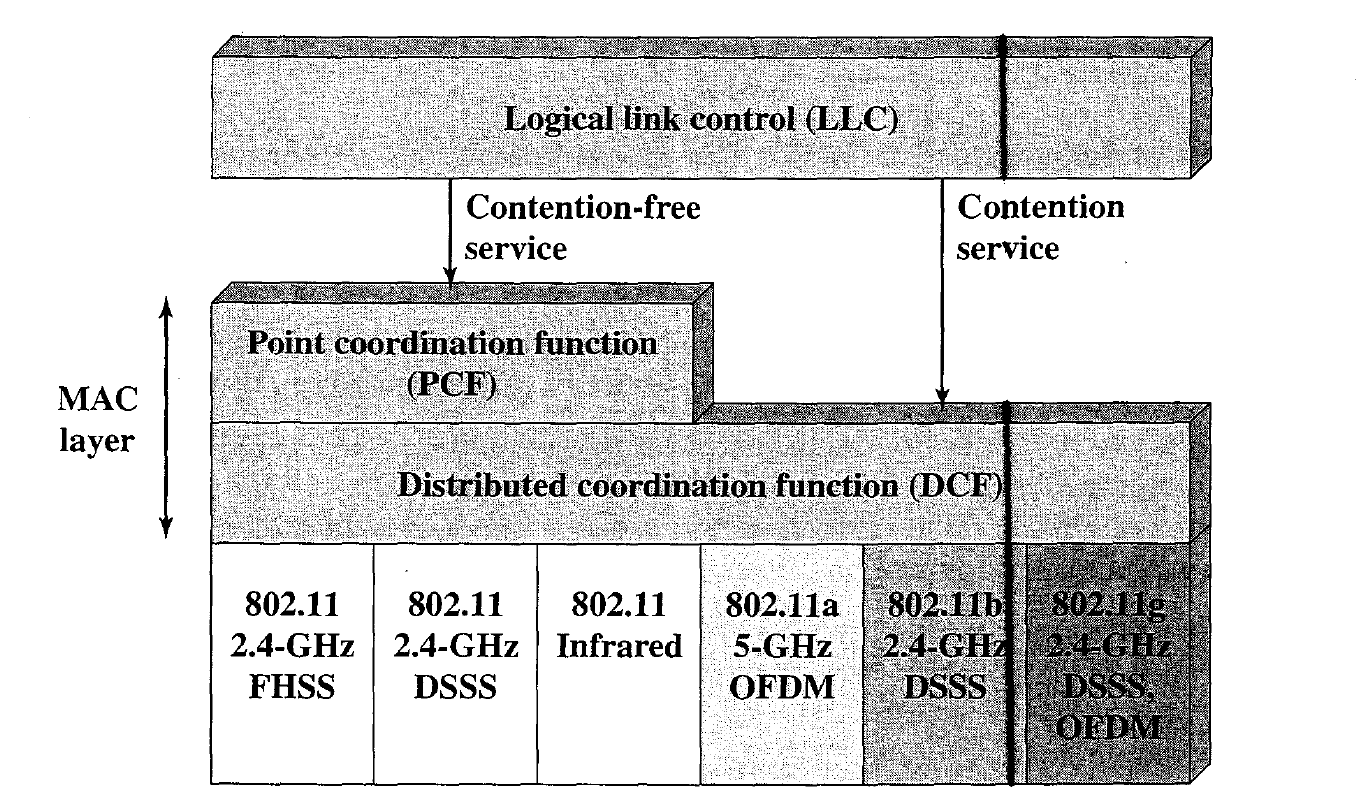
The end result for 802.11 is a MAC algorithm called DFWMAC (distribute foundation wireless MAC) that provides a distributed access control mechanism with an optional centralized control built on top of that.
Below figure illustrates the architecture. The lower sublayer of the MAC layer is the distributed coordination function (DCF). DCF uses a contention algorithm to provide access to all traffic. Ordinary asynchronous traffic directly uses DCE. The point coordination function (PCF) is a centralized MAC algorithm used to provide contention-free service. PCF is built on top of DCF and exploits features of DCF to assure access for its users. Let us consider these two sublayers in turn.
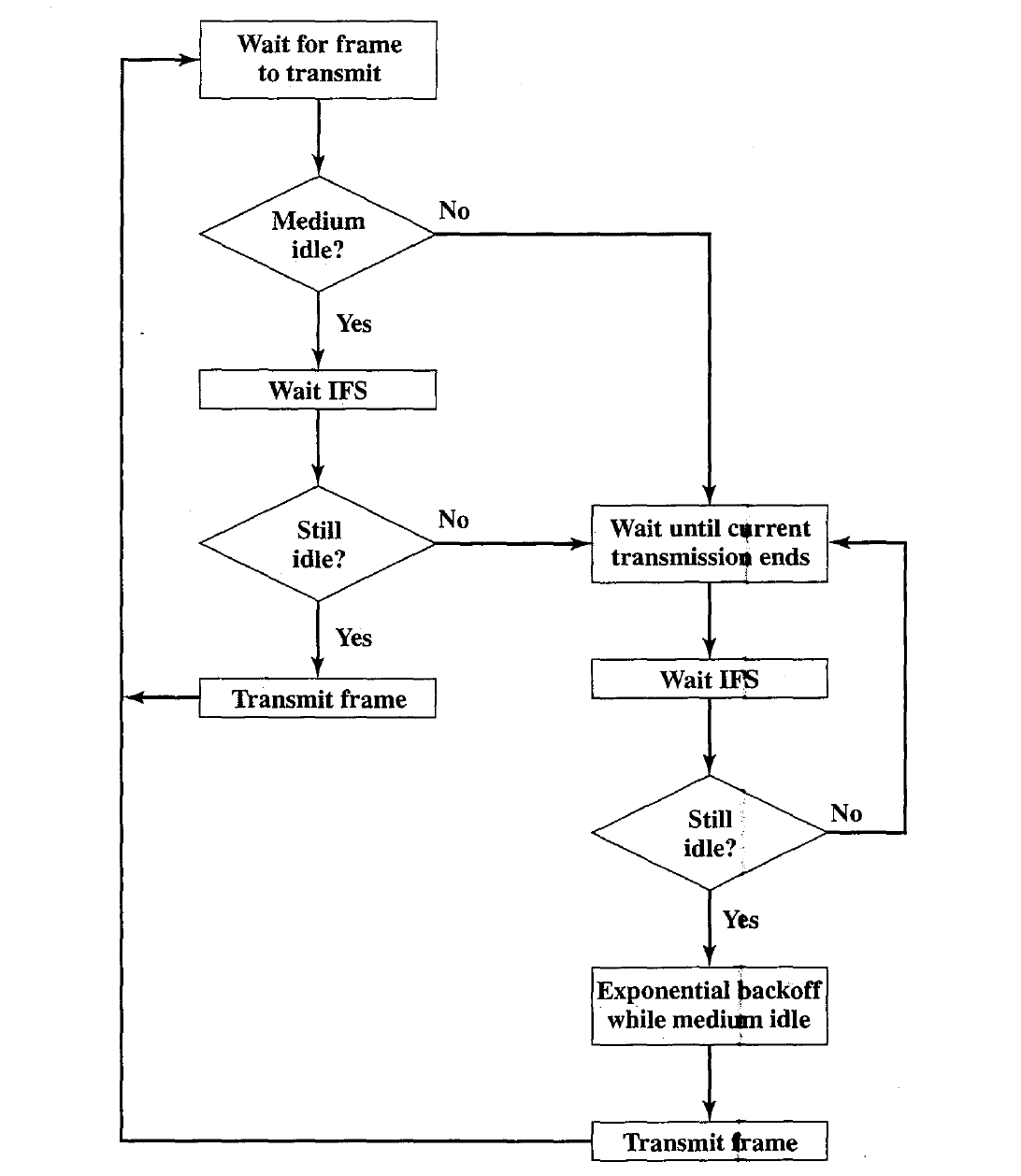
Distributed Coordination The DCF sublayer makes use of a simple CSMA (carrier sense multiple access) algorithm, which functions as follows.
If a station has a MAC frame to transmit, it listens to the medium.
If the medium is idle, the station may transmit; otherwise the station must wait until the current transmission is complete before transmitting.
The DCF does not include a collision detection function (i.e., CSMA/CD) because collision detection is not practical on a wireless network.
The dynamic range of the signals on the medium is very large, so that a transmitting station cannot effectively distinguish incoming weak signals from noise and the effects of its own transmission.
To ensure the smooth and fair functioning of this algorithm, DCF includes a set of delays that amounts to a priority scheme. Let us start by considering a single delay known as an interframe space (IFS). In fact, there are three different IFS values, but the algorithm is best explained by initially ignoring this detail.
Using an IFS, the rules for CSMA access are as follows in Below figure:
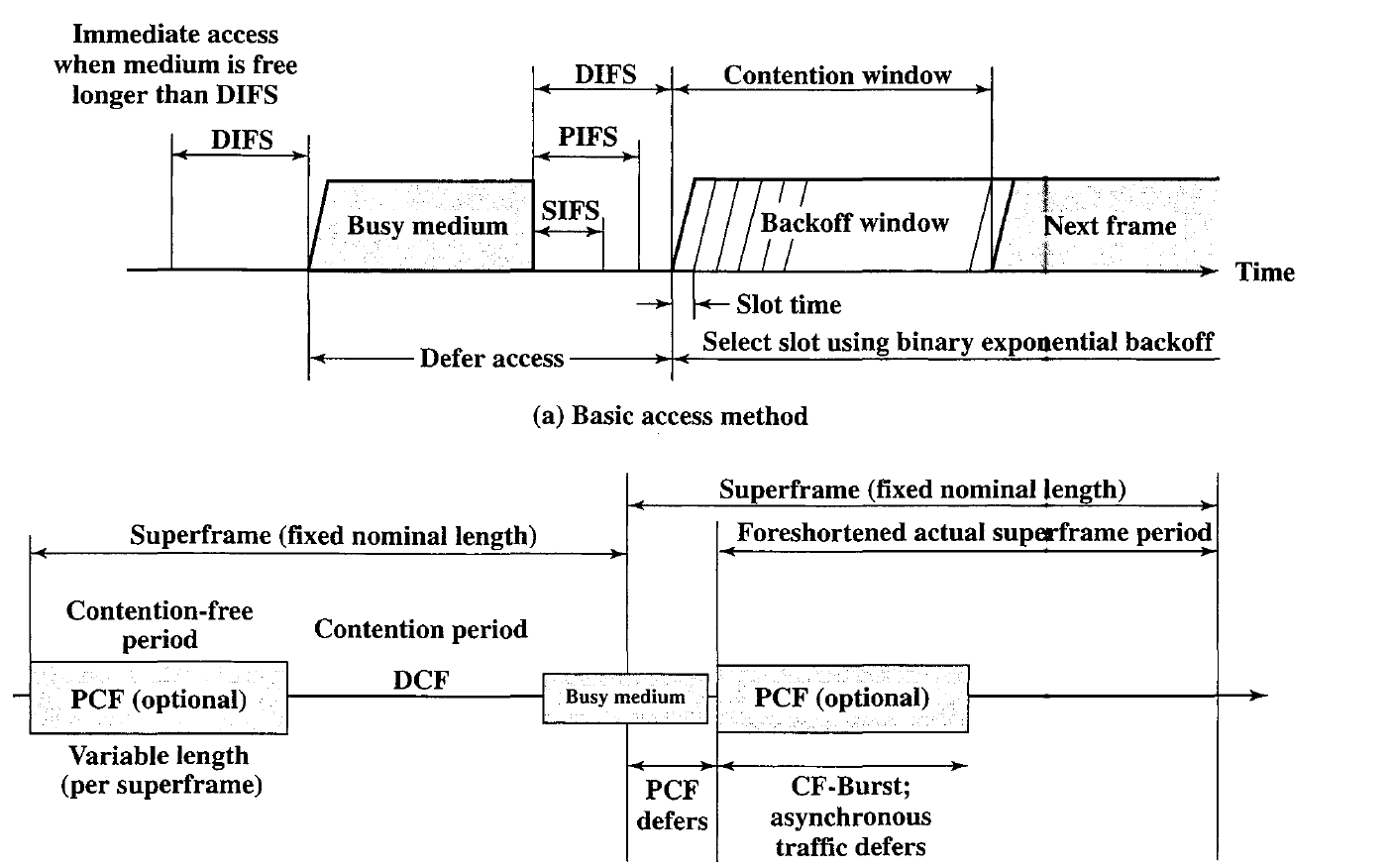
\1. A station with a frame to transmit senses the medium. If the medium is idle, it waits to see if the medium remains idle for a time equal to IFS. If so, the station may transmit immediately.
\2. If the medium is busy (either because the station initially finds the medium busy or because the medium becomes busy during the IFS idle time), the station defers transmission and continues to monitor the medium until the current transmission is over.
\3. Once the current transmission is over, the station delays another IFS. If the· medium remains idle for this period, then the station backs off a random amount of time and again senses the medium. If the medium is still idle, the station may transmit.
During the backoff time, if the medium becomes busy, the backoff timer is halted and resumes when the medium becomes idle.
\4. If the transmission is unsuccessful, which is determined by the absence of an acknowledgement, then it is assumed that a collision has occurred.
To ensure that backoff maintains stability, a technique known as binary exponential backoff is used.
A station will attempt to transmit repeatedly in the face of repeated collisions, but after each collision, the mean value of the random delay is doubled up to some maximum value.
The binary exponential backoff provides a means of handling a heavy load.
Repeated failed attempts to transmit result in longer and longer backoff times, which helps to smooth out the load. Without such a backoff, the following situation could occur.
Two or more stations attempt to transmit at the same time, causing a collision. These stations then immediately attempt to retransmit, causing a new collision.
SIFS (short IFS): The shortest IFS, used for all immediate response actions, as
explained in the following discussion
PIFS (point coordination function IFS): A midlength IFS, used by the centralized
controller in the PCF scheme when issuing polls
DIFS (distributed coordination function IFS): The longest IFS, used as a minimum
delay for asynchronous frames contending for access
Consider first the SIFS. Any station using SIFS to determine transmission opportunity has, in effect, the highest priority, because it will always gain access in preference to a station waiting an amount of time equal to PIFS or DIFS. The SIFS is used in the following circumstances:
Acknowledgment (ACK): When a station receives a frame addressed only to itself (not multicast or broadcast) it responds with an ACK frame after waiting only for an SIFS gap. This has two desirable effects. First, because collision detection is not used, the likelihood of collisions is greater than with CSMA/CD, and the MAC-level ACK provides for efficient collision recovery.
Second, the SIFS can be used to provide efficient delivery of an LLC protocol data unit (PDU) that requires multiple MAC frames. In this case, the following scenario occurs. A station with a multiframe LLC PDU to
transmit sends out the MAC frames one at a time. Each frame is acknowledged after SIFS by the recipient. When the source receives an ACK, it immediately (after SIFS) sends the next frame in the sequence.
The result is that once a station has contended for the channel, it will maintain control of the channel until it has sent all of the fragments of an LLC PDU.
Clear to Send (CTS): A station can ensure that its data frame will get through by first issuing a small Request to Send (RTS) frame.
The station to which this frame is addressed should immediately respond with a CTS frame if it is ready to receive. All other stations receive the RTS and defer using the medium.
Poll response: This is explained in the following discussion of PCP. The next longest IFS interval is the PIFS. This is used by the centralized controller in issuing polls and takes precedence over normal contention traffic.
However, those frames transmitted using SIFS have precedence over a PCF poll. Finally, the DIFS interval is used for all ordinary asynchronous traffic.
Point Coordination Function: PCF is an alternative access method implemented on top of the Dep. The operation consists of polling by the centralized polling master (point coordinator). The point coordinator makes use of PIFS when issuing polls.
Because PIFS is smaller than DIFS, the point coordinator can seize the medium and lock out all asynchronous traffic while it issues polls and receives responses.
As an extreme, consider the following possible scenario. A wireless network is configured so that a number of stations with time-sensitive traffic are controlled by the point coordinator while remaining traffic contends for access using CSMA.
The point coordinator could issue polls in a round-robin fashion to all stations configured for polling. When a poll is issued, the polled station may respond using SIFS. If the point coordinator receives a response, it issues another poll using PIFS.
If no response is received during the expected turnaround time, the coordinator issues a poll.
If the discipline of the preceding paragraph were implemented, the point coordinator would lock out all asynchronous traffic by repeatedly issuing polls. To prevent this, an interval known as the superframe is defined. During the first part of this interval, the point coordinator issues polls in a round-robin fashion to all stations configured for polling. The point coordinator then idles for the remainder of the superframe, allowing a contention period for asynchronous access.
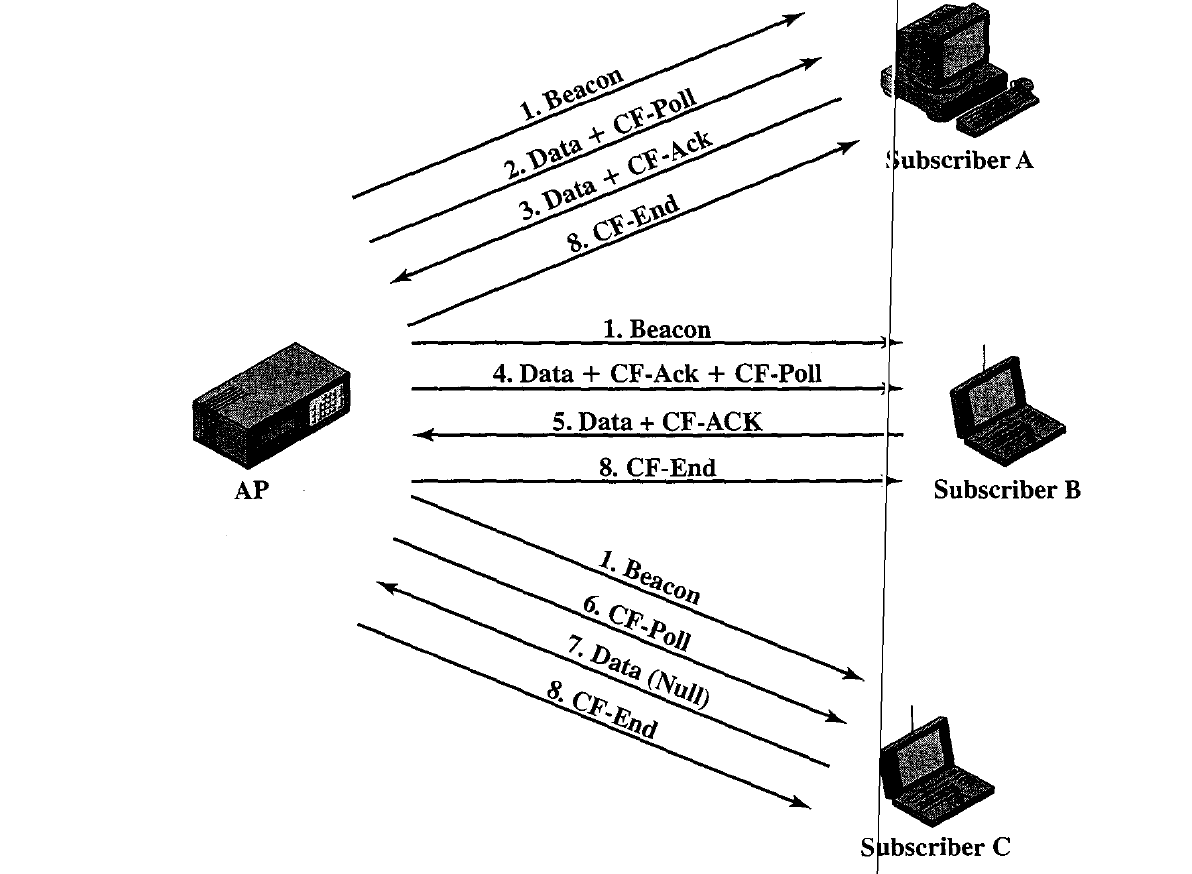
Figure illustrates the use of the superframe. At the beginning of a superframe, the point coordinator may optionally seize control and issues polls for a give period of time.
This interval varies because of the variable frame size issued by responding stations. The remainder of the superframe is available for contention based access.
At the end of the superframe interval, the point coordinator contends for access to the medium using PIFS. If the medium is idle, the point coordinator gains immediate access and a full superframe period follows. However, the medium may be busy at the end of a superframe. In this case, the point coordinator must wait until the medium is idle to gain access; this results in a foreshortened superframe period for the next cycle.
Question: Consider the sequence of actions within a BSS depicted in Figure. Draw a timeline, beginning with a period during which the medium is busy and ending with a period in which the CF-End is broadcast from the AP. Show the transmission periods and the gaps.