IEEE 802.11 protocol architecture
Published:
This post covers WIRELESS COMMUNICATIONS AND NETWORKS by William Stallings.
Basic Ideas
The Wireless LAN- Fundamental System Design
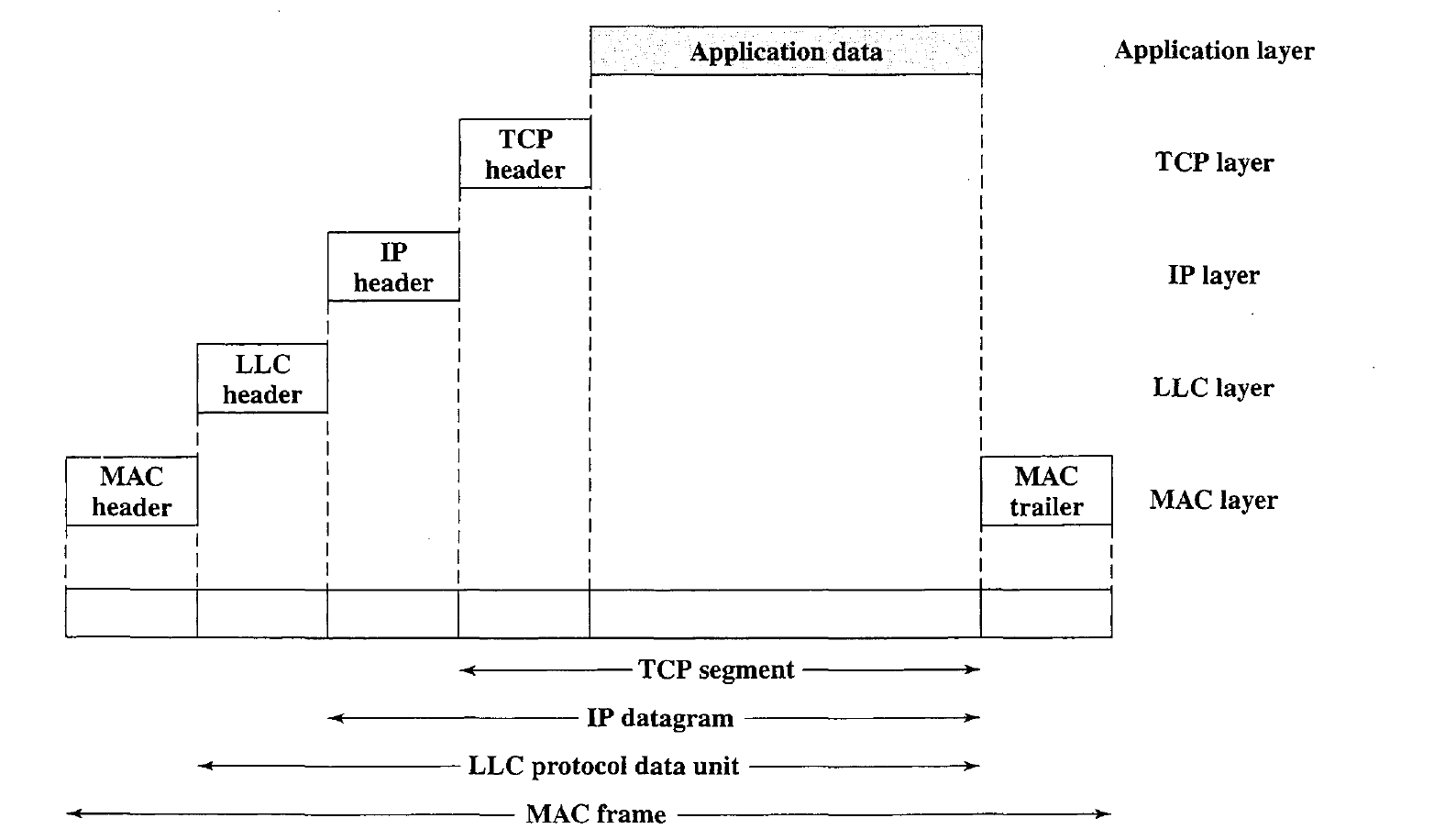
MAC Frame Format
- The MAC layer receives a block of data from the LLC layer and is responsible for performing functions related to medium access and for transmitting the data.
- As with other protocol layers, MAC implements these functions making use of a protocol data unit at its layer.
In this case, the PDU is referred to as a MAC frame.
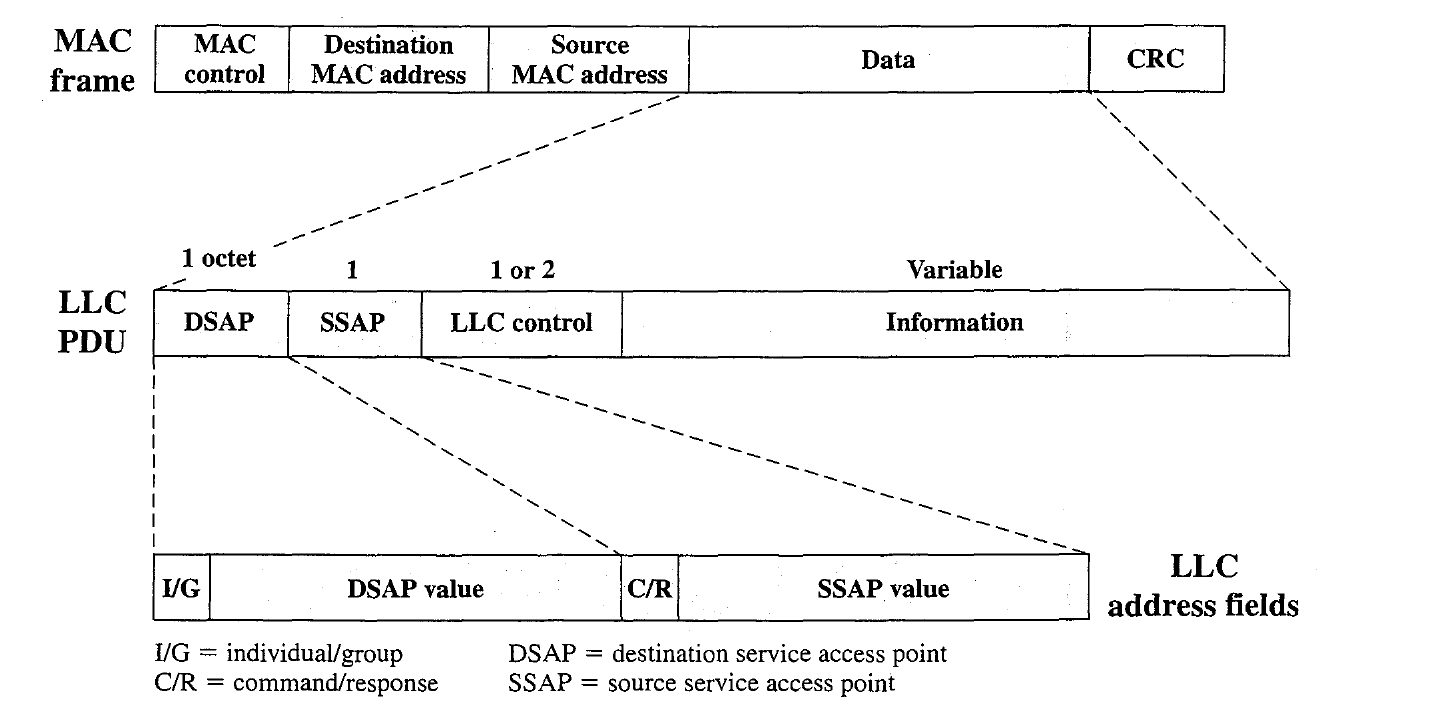
- The exact format of the MAC frame differs somewhat for the various MAC protocols in use. In general, all of the MAC frames have a format similar. The fields of this frame are as follows:
- MAC Control: This field contains any protocol control information needed fo the functioning of the MAC protocol. For example, a priority level could be indicated here.
- Destination MAC Address: The destination physical attachment point on the LAN for this frame.
- Source MAC Address: The source physical attachment point on the LAN for this frame.
- Data: The body of the MAC frame. This may be LLC data from the next higher layer or control information relevant to the operation of the MAC protocol.
- CRC: The cyclic redundancy check field (also known as the frame check sequence, PCS, field). The CRC is used in virtually all data link protocols, such as HDLC.
- In most data link control protocols, the data link protocol entity is responsible not only for detecting errors using the CRC but for recovering from those errors by retransmitting damaged frames.
- In the LAN protocol architecture, these two functions are split between the MAC and LLC layers.
- The MAC layer is responsible for detecting errors and discarding any frames that are in error.
- The LLC layer optionally keeps track of which frames have been successfully received and retransmits unsuccessful frames.
Logical Link Control
The LLC layer for LANs is similar in many respects to other link layers in common use. Like all link layers, LLC is concerned with the transmission of a link-level PDU between two stations, without the necessity of an intermediate switching node.
LLC has two characteristics not shared by most other link control protocols:
- \1. It must support the multiaccess, shared-medium nature of the link (this differs from a multidrop line in that there is no primary node).
- \2. It is relieved of some details of link access by the MAC layer.
Addressing in LLC involves specifying the source and destination LLC users.
Typically, a user is a higher-layer protocol or a network management function in the station.
These LLC user addresses are referred to as service access points (SAPs)
We look first at the services that LLC provides to a higher-level user, and then at the LLC protocol.
LLC Services LLC specifies the mechanisms for addressing stations across the medium and for controlling the exchange of data between two users.
LLC provides three alternative services for attached devices:
Unacknowledged connectionless service: This is a datagram-style service. It is a very simple service that does not involve any flow- and error-control mechanisms.
- Thus, the delivery of data is not guaranteed. However, in most devices, there will be some higher layer of software that deals with reliability issues.
Connection-mode service: A logical connection is set up between two users exchanging data, and flow control and error control are provided.
Acknowledged connectionless service: This is a cross between the previous two services. It provides that datagrams are to be acknowledged, but no priological connection is set up. Typically, a vendor will provide these services as options that the customer can select when purchasing the equipment.
Alternatively, the customer can purchase equipment that provides two or all three services and select a specific service based on application.
The unacknowledged connectionless service requires minimum logic and is useful in two contexts.
First, it will often be the case that higher layers of software will provide the necessary reliability and flow-control mechanism, and it is efficient to avoid duplicating them.
For example, TCP could provide the mechanisms needed to ensure that data are delivered reliably.
Second, there are instances in which the overhead of connection establishment and maintenance is unjustified or even counterproductive (for example, data collection activities that involve the periodic sampling of data sources, such as sensors and automatic self-test reports from security equipment or network components).
In a monitoring application, the loss of an occasional data unit would not cause distress, as the next report should arrive shortly. Thus, in most cases, the unacknowledged connectionless service is the preferred option.
The connection-mode service could be used in very simple devices, such as remote sensors, that have little software operating above this level. In these cases, it would provide the flow control and reliability mechanisms normally implemented at higher layers of the communications software.
The acknowledged connectionless service is useful in several contexts. With the connection-mode service, the logical link control software must maintain some sort of table for each active connection, to keep track of the status of that connection.
If the user needs guaranteed delivery but there is a large number of destinations for data, then the connection-mode service may be impractical because of the large number of tables required.
An example is a process control or automated factory environment Where a central site may need to communicate with a large number of processors and programmable controllers. Another use of this is the handling of important and time critical alarm or emergency control signals in a factory.
Because of their importance, an acknowledgment is needed so that the sender can be assured that the signal got through.
Because of the urgency of the signal, the user might not want to take the time first to establish a logical connection and then send the data.
LLC Protocol LLC makes use of the asynchronous balanced mode of operation of, to support connection-mode LLC service; this is referred to as type 2 operation.
LLC supports an unacknowledged connectionless service using the unnumbered information PDU; this is known as type 1 operation.
LLC supports an acknowledged connectionless service by using two new unnumbered PDUs; this is known as type 3 operation.
LLC permits multiplexing by the use of LLC service access points (LSAPs).
All three LLC protocols employ the same PDU format, which consists of four fields.
The DSAP and SSAP fields each contain a 7-bit address, which specify the destination and source users of LLC, respectively.
One bit of the DSAP indicates whether the DSAP is an individual or group address. One bit of the SSAP indicates whether the PDU is a command or response PDU.
The format of the LLC control field uses extended (7-bit) sequence numbers.
For type 1 operation, which supports the unacknowledged connectionless service, the unnumbered information (UI) PDU is used to transfer user data.
There is no acknowledgment, flow control, or error control. However, there is error detection and discard at the MAC level.
Two other PDU types, XID and TEST, are used to support management functions associated with all three types of operation.
Both PDU types are used in the following fashion. An LLC entity may issue a command (C/R bit = 0) XID or TEST.
The receiving LLC entity issues a corresponding XID or TEST in response.
The XID PDU is used to exchange two types of information: types of operation supported and window size.
The TEST PDU is used to conduct a loopback test of the transmission path between two LLC entities. Upon receipt of a TEST command PDU, the addressed LLC entity issues a TEST response PDU as soon as possible.
With type 2 operation, a data link connection is established between two LLC SAPs prior to data exchange.
Connection establishment is attempted by the type 2 protocol in response to a request from a user.
The LLC entity issues a SABME PDU2 to request a logical connection with the other LLC entity.
If the connection is accepted by the LLC user designated by the DSAP, then the destination LLC entity returns an unnumbered acknowledgment (UA) PDU. The connection is henceforth uniquely identified by the pair of user SAPs.
If the destination LLC user rejects the connection request, its LLC entity returns a disconnected mode (DM) PDU.
Once the connection is established, data are exchanged using information PDUs.
Information PDUs include send and receive sequence numbers, for sequencing and flow control. The supervisory PDUs are used, for flow control and error control.
Either LLC entity can terminate a logical LLC connection by issuing a disconnect (DISC) PDU.
With type 3 operation, each transmitted PDU is acknowledged. A new unnumbered PDU, the acknowledged connectionless (AC) information PDU, is defined.
User data are sent in AC command PDUs and must be acknowledged using an AC response PDU. To guard against lost PDUs, a I-bit sequence number is used.
The sender alternates the use of 0 and 1 in its AC command PDU, and the receiver responds with an AC PDU with the opposite number of the corresponding command. Only one PDU in each direction may be outstanding at any time