Access techniques
Published:
This post covers WIRELESS COMMUNICATIONS AND NETWORKS by William Stallings.
Basic Ideas
Protected Access- Fundamental System Design

The 802.11i architecture consists of three main ingredients:
Authentication: A protocol is used to define an exchange between a user and an AS that provides mutual authentication and generates temporary keys to be used between the client and the AP over the wireless link.
Access control: This function enforces the use of the authentication function, routes the messages properly, and facilitates key exchange. It can work with a variety of authentication protocols.
Privacy with message integrity: MAC-level data (E .g., an LLC PDU) are encrypted, along with a message integrity code that ensures that the data have not been altered.
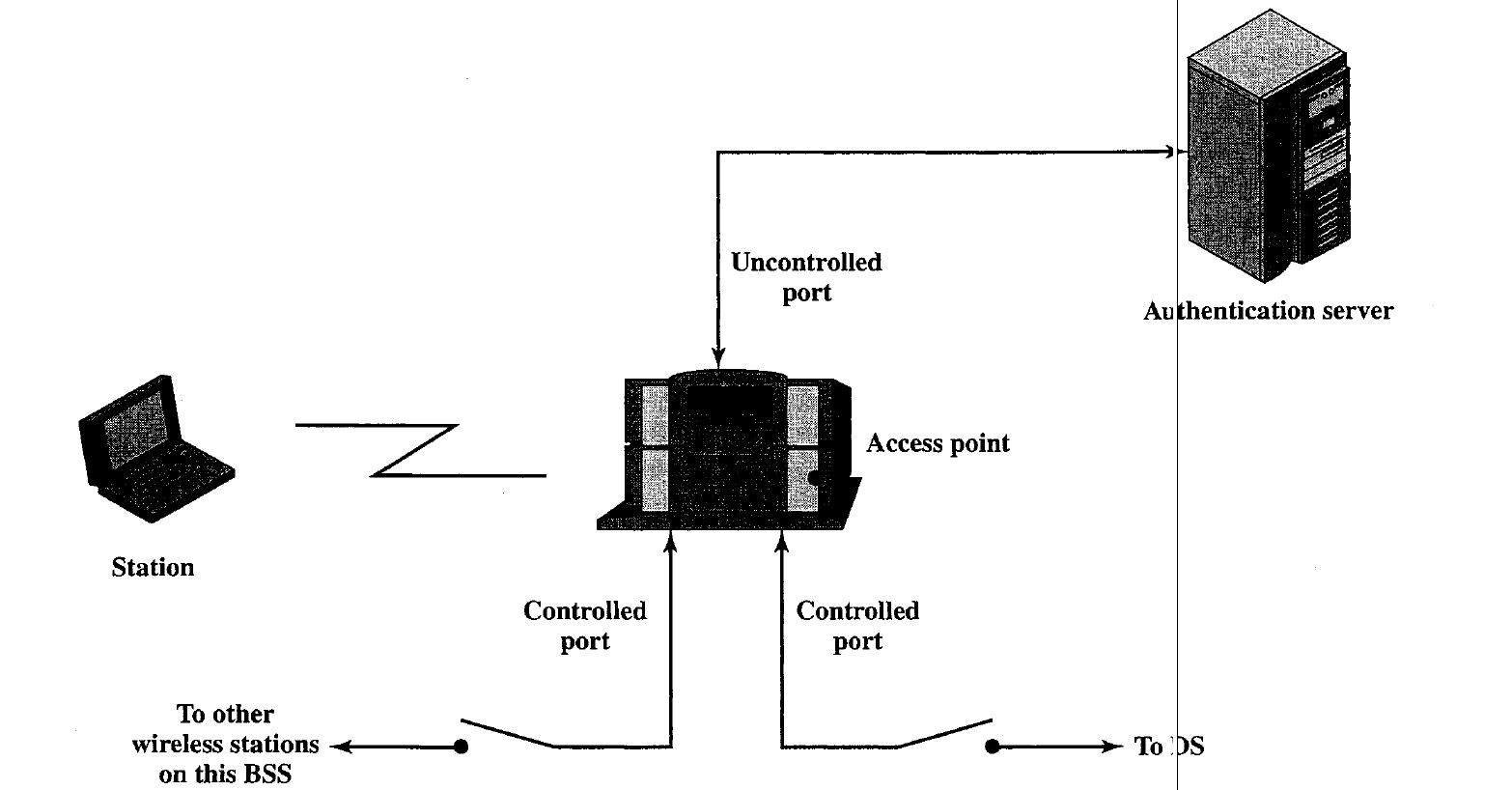
Access Control
IEEE 802.1X uses the terms supplicant, aUihenticator, and authentication server (AS). In the context of an 802.11 WLAN, the first two terms correspond to the wireless station and the AP. The AS is typically a separate device on the wired side of the network (i.e., accessible over the DS) but c uld also reside directly on the authenticator.
Before a supplicant is authenticated by the AS, using an authe tication protocol, the authenticator only passes control or authentication messal es between the supplicant and the AS; the 802.1X control channel is unblocked but the 802.11 data channel is blocked.
Once a supplicant is authenticated and keys are provided, the authenticator can forward data from the supplicant, subject to pre defined access control limitations for the supplicant to the network. Under these circumstances, the data channel is unblocked.